
When you buy a Cisco Catalyst Ethernet switch, the switch is ready to work.
All you have to do is take it out of the box, power on the switch by connecting the power cable to the switch and a power outlet, and connect hosts to the switch using the correct unshielded twisted-pair (UTP) cables.
You do not have to configure anything else, you do not have to connect to the console and login, or do anything: the switch just starts forwarding Ethernet frames.
In later lessons, you will learn how to build, configure, and verify the operation of Ethernet LANs.
In the lesson, “Using the Command-Line Interface,” you learned some skills so you know how to connect to a switch’s CLI, move around in the CLI, issue commands, and configure the switch.
The next step—this lesson—takes a short but important step in that journey by explaining the logic a switch uses when forwarding Ethernet frames.
This lesson has two major sections. The first reviews the concepts behind LAN switching, which were first introduced back in previous lesson, “Fundamentals of Ethernet LANs.”
The second section of this lesson then uses IOS show commands to verify that Cisco switches actually learned the MAC addresses, built its MAC address table, and forwarded frames.
A modern Ethernet LAN connects user devices as well as servers into some switches, with the switches then connecting to each other, sometimes in a design like Figure 1.
Part of the LAN, called a campus LAN, supports the end user population as shown on the left of the figure. End user devices connect to LAN switches, which in turn connect to other switches so that a path exists to the rest of the network.
The campus LAN switches sit in wiring closets close to the end users. On the right, the servers used to provide information to the users also connects to the LAN.
Those servers and switches often sit in a closed room called a data center, with connections to the campus LAN to support traffic to/from the users.

Figure 1: Campus LAN and Data Center LAN, Conceptual Drawing
To forward traffic from a user device to a server and back, each switch performs the same kind of logic, independently from each other.
The first half of this lesson examines the logic: how a switch chooses to forward an Ethernet frame, when the switch chooses to not forward the frame, and so on.
Ultimately, the role of a LAN switch is to forward Ethernet frames.
LANs exist as a set of user devices, servers, and other devices that connect to switches, with the switches connected to each other. The LAN switch has one primary job: to forward frames to the correct destination (MAC) address.
And to achieve that goal, switches use logic—logic based on the source and destination MAC address in each frame’s Ethernet header.
LAN switches receive Ethernet frames and then make a switching decision: either forward the frame out some other ports or ignore the frame. To accomplish this primary mission, switches perform three actions:
The first action is the switch’s primary job, whereas the other two items are overhead functions.
NOTE: Throughout our discussion of LAN switches, the terms switch port and switch interface are synonymous.
Although previous lessons already discussed the frame format, this discussion of Ethernet switching is pretty important, so reviewing the Ethernet frame at this point might be helpful.
Figure 2 shows one popular format for an Ethernet frame.
Basically, a switch would take the frame shown in the figure, make a decision of where to forward the frame, and send the frame out that other interface.

Figure 2: IEEE 802.3 Ethernet Frame (One Variation)
Most of the upcoming discussions and figures about Ethernet switching focuses on the use of the destination and source MAC address fields in the header.
All Ethernet frames have both a destination and source MAC address.
Both are 6-bytes long (represented as 12 hex digits), and are a key part of the switching logic discussed in this section.
To decide whether to forward a frame, a switch uses a dynamically built table that lists MAC addresses and outgoing interfaces. Switches compare the frame’s destination MAC address to this table to decide whether the switch should forward a frame or simply ignore it.
For example, consider the simple network shown in Figure 3, with Fred sending a frame to Barney.

Figure 3: Sample Switch Forwarding and Filtering Decision
In this figure, Fred sends a frame with destination address 0200.2222.2222 (Barney’s MAC address).
The switch compares the destination MAC address (0200.2222.2222) to the MAC address table, matching the bold table entry.
That matched table entry tells the switch to forward the frame out port F0/2, and only port F0/2.
NOTE: A switch’s MAC address table is also called the switching table, or bridging table, or even the Content-Addressable Memory (CAM) table, in reference to the type of physical memory used to store the table.
A switch’s MAC address table lists the location of each MAC relative to that one switch. In LANs with multiple switches, each switch makes an independent forwarding decision based on its own MAC address table. Together, they forward the frame so that it eventually arrives at the destination.
For example, Figure 4 shows the first switching decision in a case in which Fred sends a frame to Wilma, with destination MAC 0200.3333.3333.
The topology has changed versus the previous figure, this time with two switches, and Fred and Wilma connected to two different switches.
Figure 3 shows the first switch’s logic, in reaction to Fred sending the original frame. Basically, the switch receives the frame in port F0/1, finds the destination MAC (0200.3333.3333) in the MAC address table, sees the outgoing port of G0/1, so SW1 forwards the frame out its G0/1 port.

Figure 4: Forwarding Decision with Two Switches: First Switch
That same frame next arrives at switch SW2, entering SW2’s G0/2 interface.
As shown in Figure 5, SW2 uses the same logic steps, but using SW2’s table. The MAC table lists the forwarding instructions for that switch only. In this case, switch SW2 forwards the frame out its F0/3 port, based on SW2’s MAC address table.

Figure 5: Forwarding Decision with Two Switches: Second Switch
NOTE: The forwarding choice by a switch was formerly called a forward-versus-filter decision, because the switch also chooses to not forward (to filter) frames, not sending the frame out some ports.
The examples so far use switches that happen to have a MAC table with all the MAC addresses listed.
As a result, the destination MAC address in the frame is known to the switch. The frames are called known unicast frames, or simply known unicasts, because the destination address is a unicast address, and the destination is known.
As shown in these examples, switches forward known unicast frames out one port: the port as listed in the MAC table entry for that MAC address.
Thankfully, the networking staff does not have to type in all those MAC table entries. Instead, the switches do their second main function: to learn the MAC addresses and interfaces to put into its address table.
With a complete MAC address table, the switch can make accurate forwarding and filtering decisions as just discussed.
Switches build the address table by listening to incoming frames and examining the source MAC address in the frame. If a frame enters the switch and the source MAC address is not in the MAC address table, the switch creates an entry in the table. That table entry lists the interface from which the frame arrived. Switch learning logic is that simple.
Figure 6 depicts the same single-switch topology network as Figure 3, but before the switch has built any address table entries.
The figure shows the first two frames sent in this network—first a frame from Fred, addressed to Barney, and then Barney’s response, addressed to Fred.

Figure 6: Switch Learning: Empty Table and Adding Two Entries
(Figure 6 depicts the MAC learning process only, and ignores the forwarding process and therefore ignores the destination MAC addresses.)
Focus on the learning process and how the MAC table grows at each step as shown on the right side of the figure.
The switch begins with an empty MAC table, as shown in the upper right part of the figure. Then Fred sends his first frame (labeled “1”) to Barney, so the switch adds an entry for 0200.1111.1111, Fred’s MAC address, associated with interface F0/1.
Why F0/1? The frame sent by Fred entered the switch’s F0/1 port. SW1’s logic runs something like this: “The source is MAC 0200.1111.1111, the frame entered F0/1, so from my perspective, 0200.1111.1111 must be reachable out my port F0/1.”
Continuing the example, when Barney replies in Step 2, the switch adds a second entry, this one for 0200.2222.2222, Barney’s MAC address, along with interface F0/2. Why F0/2? The frame Barney sent entered the switch’s F0/2 interface. Learning always occurs by looking at the source MAC address in the frame, and adds the incoming interface as the associated port.
Now again turn your attention to the forwarding process, using the topology in Figure 5. What do you suppose the switch does with Fred’s first frame, the one that occurred when there were no entries in the MAC address table?
As it turns out, when there is no matching entry in the table, switches forward the frame out all interfaces (except the incoming interface) using a process called flooding. And the frame whose destination address is unknown to the switch is called an unknown unicast frame, or simply an unknown unicast.
Switches flood unknown unicast frames. Flooding means that the switch forwards copies of the frame out all ports, except the port on which the frame was received.
The idea is simple: if you do not know where to send it, send it everywhere, to deliver the frame. And, by the way, that device will likely then send a reply—and then the switch can learn that device’s MAC address, and forward future frames out one port as a known unicast frame.
Switches also flood LAN broadcast frames (frames destined to the Ethernet broadcast address of FFFF.FFFF.FFFF), because this process helps deliver a copy of the frame to all devices in the LAN.
For example, Figure 7 shows the same first frame sent by Fred, when the switch’s MAC table is empty. At step 1, Fred sends the frame. At step 2, the switch sends a copy of the frame out all three of the other interfaces.

Figure 7: Switch Flooding: Unknown Unicast Arrives, Floods out Other Ports
The third primary feature of LAN switches is loop prevention, as implemented by Spanning Tree Protocol (STP). Without STP, any flooded frames would loop for an indefinite period of time in Ethernet networks with physically redundant links.
To prevent looping frames, STP blocks some ports from forwarding frames so that only one active path exists between any pair of LAN segments.
The result of STP is good: Frames do not loop infinitely, which makes the LAN usable. However, STP has negative features as well, including the fact that it takes some work to balance traffic across the redundant alternate links.
A simple example makes the need for STP more obvious. Remember, switches flood unknown unicast frames and broadcast frames.
Figure 8 shows an unknown unicast frame, sent by Larry to Bob, which loops forever because the network has redundancy but no STP. Note that the figure shows one direction of the looping frame only, just to reduce clutter, but a copy of the frame would also loop the other direction as well.

Figure 8: Network with Redundant Links but Without STP: The Frame Loops Forever
The flooding of this frame would cause the frame to rotate around the three switches, because none of the switches list Bob’s MAC address in their address tables, each switch floods the frame.
And while the flooding process is a good mechanism for forwarding unknown unicasts and broadcasts, the continual flooding of traffic frames as in the figure can completely congest the LAN to the point of making it unusable.
A topology like Figure 8, with redundant links, is good, but we need to prevent the bad effect of those looping frames. To avoid Layer 2 loops, all switches need to use STP. STP causes each interface on a switch to settle into either a blocking state or a forwarding state.
Blocking means that the interface cannot forward or receive data frames, while forwarding means that the interface can send and receive data frames. If a correct subset of the interfaces is blocked, only a single currently active logical path exists between each pair of LANs.
NOTE: STP behaves identically for a transparent bridge and a switch. Therefore, the terms bridge, switch, and bridging device all are used interchangeably when discussing STP.
Switches use Layer 2 logic, examining the Ethernet data-link header to choose how to process frames. In particular, switches make decisions to forward and filter frames, learn MAC addresses, and use STP to avoid loops, as follows:
A Cisco Catalyst switch comes from the factory ready to switch frames. All you have to do is connect the power cable, plug in the Ethernet cables, and the switch starts switching incoming frames.
Connect multiple switches together, and they are ready to forward frames between the switches as well. And the big reason behind this default behavior has to do with the default settings on the switches.
Cisco Catalyst switches come ready to get busy switching frames because of settings like these:
To see a switches MAC address table, use the show mac address-table command.
With no additional parameters, this command lists all known MAC addresses in the MAC table, including some overhead static MAC addresses that you can ignore.
To see all the dynamically learned MAC addresses only, instead use the show mac address-table dynamic command.
The examples in this lesson use almost no configuration, as if you just unboxed the switch when you first purchased it.
For the examples, the switches have no configuration other than the hostname command to set a meaningful hostname.
Note that to do this in lab:
Example 1 show mac address-table dynamic for Figure 7.

Example 1: show mac address-table dynamic
First, focus on two columns of the table: the Mac Address and Ports columns of the table. The values should look familiar: they match the earlier single-switch example, as repeated here as Figure 9.
Note the four MAC addresses listed, along with their matching ports, as shown in the figure.

Figure 9: Single Switch Topology Used in Verification Section
Next, look at the Type field in the header. The column tells us whether the MAC address was learned by the switch as described earlier in this lesson.
You can also statically predefine MAC table entries using a couple of different features, including port security, and those would appear as Static in the Type column.
Finally, the VLAN column of the output gives us a chance to briefly discuss how VLANs impact switching logic. LAN switches forward Ethernet frames inside a VLAN.
What that means is if a frame enters via a port in VLAN 1, then the switch will forward or flood that frame out other ports in VLAN 1 only, and not out any ports that happen to be assigned to another VLAN.
Details of VLANs will be discuss in other lessons.
The first example assumes that you installed the switch and cabling correctly, and that the switch interfaces work. Once you do the installation and connect to the Console, you can easily check the status of those interfaces with the show interfaces status command, as shown in Example 2.


Example 2: show interfaces status on Switch SW1
Focus on the port column for a moment.
As a reminder, Cisco Catalyst switches name their ports based on the fastest specification supported, so in this case, the switch has 24 interfaces named Fast Ethernet, and two named Gigabit Ethernet.
Many commands abbreviate those terms, this time as Fa for Fast Ethernet and Gi for Gigabit Ethernet. (The example happens to come from a Cisco Catalyst switch that has 24 10/100 ports and two 10/100/1000 ports.)
The Status column of course tells us the status or state of the port. In this case, the lab switch had cables and devices connected to ports F0/1–F0/4 only, with no other cables connected. As a result, those first four ports have a state of connected, meaning that the ports have a cable and are functional.
The notconnect state means that the port is not yet functioning. It may mean that there is no cable installed, but other problems may exist as well.
NOTE: You can see the status for a single interface in a couple of ways. For instance, for F0/1, the command show interfaces f0/1 status lists the status in a single line of output as in Example 2. The show interfaces f0/1 command (without the status keyword) displays a detailed set of messages about the interface.
The show interfaces command has a large number of options. One particular option, the counters option, lists statistics about incoming and outgoing frames on the interfaces. In particular, it lists the number of unicast, multicast, and broadcast frames both the in and out direction, and a total byte count for those frames.
Example 3 shows an example, again for interface F0/1.

Example 3: show interfaces f0/1 counters on Switch SW1
With a single switch and only four hosts connected to them, you can just read the details of the MAC address table and find the information you want to see.
However, in real networks, with lots of interconnected hosts and switches, just reading the output to find one MAC address can be hard to do. You might have hundreds of entries—page after page of output—with each MAC address looking like a random string of hex characters.
Thankfully, Cisco IOS supplies several more options on the show mac address-table command to make it easier to find individual entries.
First, if you know the MAC address, you can search for it—just type in the MAC address at the end of the command, as shown in Example 4.
All you have to do is include the address keyword, followed by the actual MAC address. If the address exists, the output lists the address. Note that the output lists the exact same information in the exact same format, but it lists only the line for the matching MAC address.

Example 4: show mac address-table dynamic with the address keyword
While useful, often times the engineer troubleshooting a problem does not know the MAC addresses of the devices connected to the network. Instead, the engineer has a topology diagram, knowing which switch ports connect to other switches and which connect to endpoint devices.
Sometimes you might be troubleshooting while looking at a network topology diagram, and want to look at all the MAC addresses learned off a particular port. IOS supplies that option with the show mac address-table dynamic interface command.
Example 5 shows one example, for switch SW1’s F0/1 interface.

Example 5: show mac address-table dynamic with the interface Keyword
Finally, you may also want to find the MAC address table entries for one VLAN. You guessed it—you can add the vlan parameter, followed by the VLAN number. Example 6 shows two such examples from the same switch SW1 from Figure 7—one for VLAN 1, where all four devices reside, and one for a non-existent VLAN 2.

Example 6: The show mac address-table vlan command
This lesson closes with a few comments about how switches manage their MAC address tables.
Switches do learn MAC addresses, but those MAC addresses do not remain in the table indefinitely. The switch will remove the entries due to age, due to the table filling, and you can remove entries using a command.
First, for aging out MAC table entries, switches remove entries that have not been used for a defined number of seconds (default of 300 seconds on many switches). To do that, switches look at every incoming frame, every source MAC address, and does something related to learning.
If it is a new MAC address, the switch adds the correct entry to the table of course. However, if that entry already exists, the switch still does something: it resets the inactivity timer back to 0 for that entry. Each entry’s timer counts upward over time to measure how long the entry has been in the table. The switch times out (removes) any entries whose timer reaches the defined aging time.
Example 7 shows the aging timer setting for the entire switch. The aging time can be configured to a different time, globally and per-vlan.

Example 7: The MAC Address Default Aging Timer Displayed
Each switch also removes the oldest table entries, even if they are younger than the aging time setting, if the table fills. The MAC address table uses content-addressable memory (CAM), a physical memory that has great table lookup capabilities.
However, the size of the table depends on the size of the CAM in a particular model of switch. When a switch tries to add a new table entry, and finds the table full, the switch times out (removes) the oldest table entry to make space.
For perspective, the end of Example 7 lists the size of a Cisco Catalyst switch’s MAC table at about 8000 entries—the same four existing entries from the earlier examples, with space for 7299 more.
Finally, you can remove the dynamic entries from the MAC address table with the clear mac address-table dynamic command. Note that the show commands in this lesson can be executed from user and enable mode, but the clear command happens to be a privileged mode command.
Finally, to complete the discussion, it helps to think about an example with multiple switches, just to emphasize how MAC learning, forwarding, and flooding happens independently on each LAN switch.
Consider the topology in Figure 10, and pay close attention to the port numbers. The ports were purposefully chosen so that neither switch used any of the same ports for this example. That is, switch SW2 does have a port F0/1 and F0/2, but I did not plug any devices into those ports when making this example.
Also note that all ports are in VLAN 1, and as with the other examples in this lesson, all default configuration is used other than the hostname on the switches.

Figure 10: Two-Switch Topology Example
Think about a case in which both switches learn all four MAC addresses. For instance, that would happen if the hosts on the left communicate with the hosts on the right.
SW1’s MAC address table would list SW1’s own port numbers (F0/1, F0/2, and G0/1), because SW1 uses that information to decide where SW1 should forward frames. Similarly, SW2’s MAC table lists SW2’s port numbers (F0/3, F0/4, G0/2 in this example).
Example 8 shows the MAC address tables on both switches for that scenario.
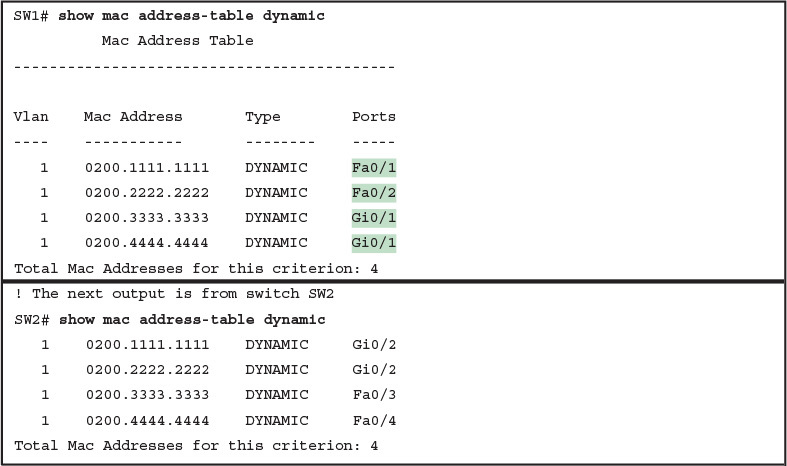
Example 8: The MAC Address Table on Two Switches